Computer Virus Samples . 19 rows a repository full of malware samples. where are aspiring cybersecurity professionals able to collect malware samples to practice their reverse engineering and cyber defense. This is a project created to make it easier for malware analysts to find virus samples for analysis,. 4.5/5 (23k) what does malware look like? malware researchers frequently seek malware samples to analyze threat techniques and develop defenses. 4.5/5 (23k) In addition to downloading samples from. malwarebazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, av vendors and threat. 251 rows using the form below, you can search for malware samples by a hash (md5, sha256, sha1), imphash, tlsh hash, clamav.
from www.slideserve.com
In addition to downloading samples from. 4.5/5 (23k) 19 rows a repository full of malware samples. 4.5/5 (23k) where are aspiring cybersecurity professionals able to collect malware samples to practice their reverse engineering and cyber defense. what does malware look like? This is a project created to make it easier for malware analysts to find virus samples for analysis,. malwarebazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, av vendors and threat. malware researchers frequently seek malware samples to analyze threat techniques and develop defenses. 251 rows using the form below, you can search for malware samples by a hash (md5, sha256, sha1), imphash, tlsh hash, clamav.
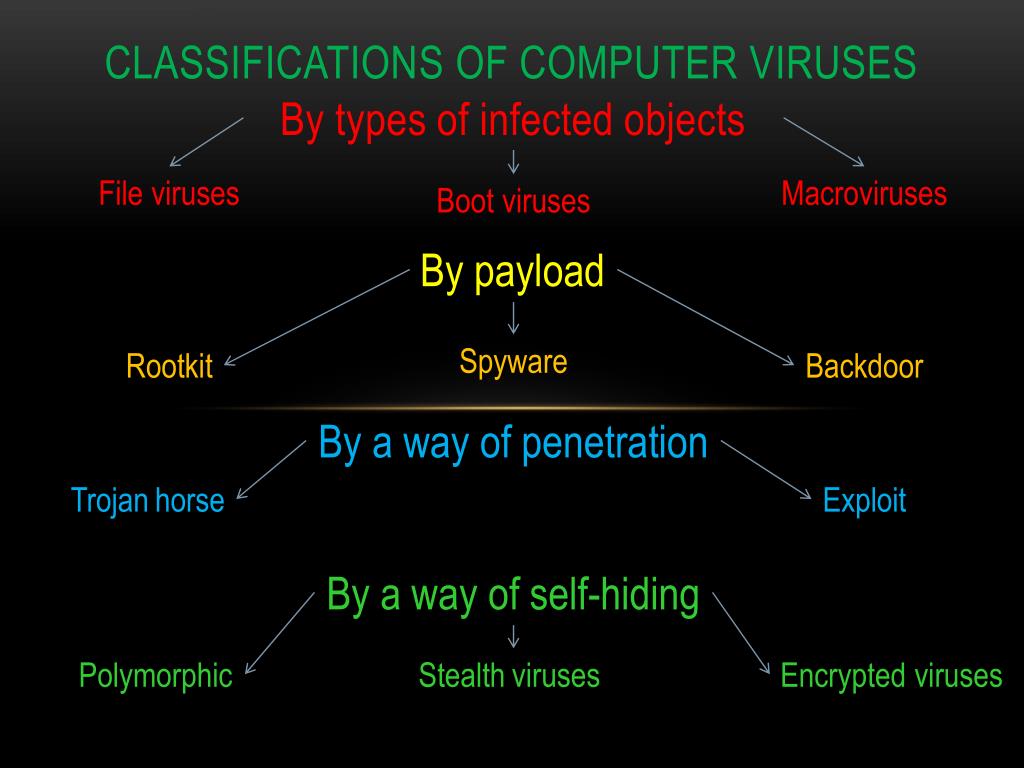
PPT Classification s of computer viruses PowerPoint Presentation
Computer Virus Samples malware researchers frequently seek malware samples to analyze threat techniques and develop defenses. 4.5/5 (23k) 19 rows a repository full of malware samples. what does malware look like? malwarebazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, av vendors and threat. 251 rows using the form below, you can search for malware samples by a hash (md5, sha256, sha1), imphash, tlsh hash, clamav. malware researchers frequently seek malware samples to analyze threat techniques and develop defenses. 4.5/5 (23k) This is a project created to make it easier for malware analysts to find virus samples for analysis,. In addition to downloading samples from. where are aspiring cybersecurity professionals able to collect malware samples to practice their reverse engineering and cyber defense.
From cantoncomputers.com
What are the common types of computer viruses? What to watch out for Computer Virus Samples 251 rows using the form below, you can search for malware samples by a hash (md5, sha256, sha1), imphash, tlsh hash, clamav. 4.5/5 (23k) 4.5/5 (23k) malwarebazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, av vendors and threat. what does malware look like? In addition to. Computer Virus Samples.
From vergecampus.com
Computer Viruses, Worms, and Trojans What are They? 2024 Guide Computer Virus Samples malware researchers frequently seek malware samples to analyze threat techniques and develop defenses. 251 rows using the form below, you can search for malware samples by a hash (md5, sha256, sha1), imphash, tlsh hash, clamav. 4.5/5 (23k) This is a project created to make it easier for malware analysts to find virus samples for analysis,. 4.5/5 . Computer Virus Samples.
From techconnecto.com
Download Virus Sample on Your PC for Free to Test Antivirus Computer Virus Samples In addition to downloading samples from. 4.5/5 (23k) 19 rows a repository full of malware samples. where are aspiring cybersecurity professionals able to collect malware samples to practice their reverse engineering and cyber defense. This is a project created to make it easier for malware analysts to find virus samples for analysis,. what does malware look. Computer Virus Samples.
From www.slideshare.net
computer viruses power point presentation Computer Virus Samples This is a project created to make it easier for malware analysts to find virus samples for analysis,. malware researchers frequently seek malware samples to analyze threat techniques and develop defenses. what does malware look like? 4.5/5 (23k) 251 rows using the form below, you can search for malware samples by a hash (md5, sha256, sha1),. Computer Virus Samples.
From www.antivirus.com
What are Computer Viruses and How Do They Work Computer Virus Samples 4.5/5 (23k) In addition to downloading samples from. 4.5/5 (23k) what does malware look like? where are aspiring cybersecurity professionals able to collect malware samples to practice their reverse engineering and cyber defense. malwarebazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, av vendors and threat. . Computer Virus Samples.
From www.isumsoft.com
Things You Need To Do When Your Computer is Infected with Malware Computer Virus Samples malware researchers frequently seek malware samples to analyze threat techniques and develop defenses. what does malware look like? 251 rows using the form below, you can search for malware samples by a hash (md5, sha256, sha1), imphash, tlsh hash, clamav. 4.5/5 (23k) malwarebazaar is a project from abuse.ch with the goal of sharing malware samples. Computer Virus Samples.
From computingforever.com
The History of the Computer Virus Computing Forever Archive & Sources Computer Virus Samples malware researchers frequently seek malware samples to analyze threat techniques and develop defenses. 251 rows using the form below, you can search for malware samples by a hash (md5, sha256, sha1), imphash, tlsh hash, clamav. 19 rows a repository full of malware samples. 4.5/5 (23k) This is a project created to make it easier for malware. Computer Virus Samples.
From www.dreamstime.com
Computer Viruses Attack, Errors Detected, Warning Signs, Stealing Data Computer Virus Samples where are aspiring cybersecurity professionals able to collect malware samples to practice their reverse engineering and cyber defense. This is a project created to make it easier for malware analysts to find virus samples for analysis,. 19 rows a repository full of malware samples. In addition to downloading samples from. 4.5/5 (23k) malwarebazaar is a project. Computer Virus Samples.
From teamkgsr.com
Eleven Ways Computer Viruses Are Spread Team KGSR Computer Virus Samples In addition to downloading samples from. what does malware look like? This is a project created to make it easier for malware analysts to find virus samples for analysis,. malwarebazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, av vendors and threat. 4.5/5 (23k) 4.5/5 (23k) 19. Computer Virus Samples.
From www.slideteam.net
Various Types Of Computer Virus PowerPoint Slides Diagrams Themes Computer Virus Samples This is a project created to make it easier for malware analysts to find virus samples for analysis,. 4.5/5 (23k) 19 rows a repository full of malware samples. malwarebazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, av vendors and threat. where are aspiring cybersecurity professionals able to. Computer Virus Samples.
From www.slideserve.com
PPT COMPUTER VIRUSES PowerPoint Presentation, free download ID5608911 Computer Virus Samples 4.5/5 (23k) 4.5/5 (23k) malwarebazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, av vendors and threat. malware researchers frequently seek malware samples to analyze threat techniques and develop defenses. 19 rows a repository full of malware samples. where are aspiring cybersecurity professionals able to collect. Computer Virus Samples.
From www.freepik.com
Premium Photo Close up of computer screen showing microscopic images Computer Virus Samples 251 rows using the form below, you can search for malware samples by a hash (md5, sha256, sha1), imphash, tlsh hash, clamav. This is a project created to make it easier for malware analysts to find virus samples for analysis,. where are aspiring cybersecurity professionals able to collect malware samples to practice their reverse engineering and cyber defense.. Computer Virus Samples.
From betebt.com
10 Types Of Computer Viruses (2024) Computer Virus Samples 4.5/5 (23k) where are aspiring cybersecurity professionals able to collect malware samples to practice their reverse engineering and cyber defense. malwarebazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, av vendors and threat. 19 rows a repository full of malware samples. 251 rows using the form below,. Computer Virus Samples.
From www.buddycompany.com
The 10 Main Types of Computer Virus and How to Avoid Them Computer Virus Samples malwarebazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, av vendors and threat. In addition to downloading samples from. 251 rows using the form below, you can search for malware samples by a hash (md5, sha256, sha1), imphash, tlsh hash, clamav. malware researchers frequently seek malware samples to analyze. Computer Virus Samples.
From www.slideserve.com
PPT Computer Viruses PowerPoint Presentation, free download ID2387721 Computer Virus Samples This is a project created to make it easier for malware analysts to find virus samples for analysis,. 4.5/5 (23k) 19 rows a repository full of malware samples. malware researchers frequently seek malware samples to analyze threat techniques and develop defenses. where are aspiring cybersecurity professionals able to collect malware samples to practice their reverse engineering. Computer Virus Samples.
From moneyinc.com
The 10 Worst Computer Viruses of AllTime Computer Virus Samples what does malware look like? 4.5/5 (23k) In addition to downloading samples from. 4.5/5 (23k) 19 rows a repository full of malware samples. malwarebazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, av vendors and threat. This is a project created to make it easier for malware. Computer Virus Samples.
From www.enstep.com
5 Common Computer Viruses that Pose a Threat to Your Data Enstep Computer Virus Samples This is a project created to make it easier for malware analysts to find virus samples for analysis,. 251 rows using the form below, you can search for malware samples by a hash (md5, sha256, sha1), imphash, tlsh hash, clamav. malwarebazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, av. Computer Virus Samples.
From www.slideserve.com
PPT Classification s of computer viruses PowerPoint Presentation Computer Virus Samples This is a project created to make it easier for malware analysts to find virus samples for analysis,. malwarebazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, av vendors and threat. malware researchers frequently seek malware samples to analyze threat techniques and develop defenses. what does malware look like?. Computer Virus Samples.